Hi all,
Recently I have found an Insecure Direct Object Issue on Nokia. I have already reported this issue and also got fixed.
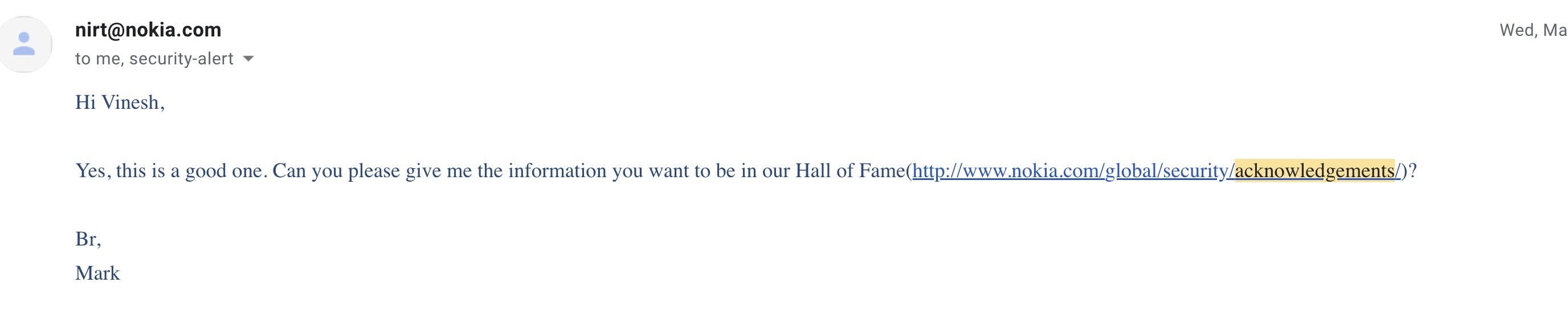
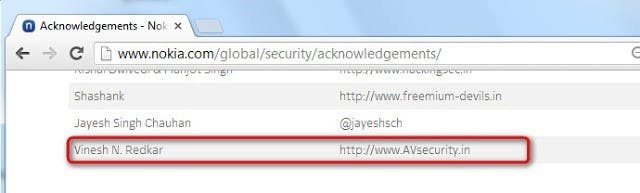
Thanks to Nokia developer Team. They have listed my name on the Nokia Hall Of Fame List on the below-mentioned URL: nokia.com/global/security/acknowledgements

Before we start discussing the issue we will first look into what Insecure Direct Object Reference is?
#What is Insecure Direct Object Reference? The Insecure Direct Object References represent the flaws in system design where access to sensitive data/assets is not fully protected and data objects are exposed by the application with the assumption that the user will always follow the application rules.
Insecure Direct Object Reference is an attack where an attacker who is an authenticated system user, simply changes a parameter value that directly refers to a system object or another object the user isn’t authorized for.
- Authentication: Authentication verifies who you are.
- Authorization: Authorization verifies what you are authorized to do.
OWASP Definition For Insecure Direct Object Reference
A direct object reference occurs when a developer exposes a reference to an internal implementation object, such as a file, directory, database record, or key, as a URL or form parameter. An attacker can manipulate direct object references to access other objects without authorization unless an access control check is in place.
How to identify Insecure Direct Object Reference? Identifying this vulnerability is slightly more difficult using Automation tools than other vulnerabilities because to exploit this vulnerability you not only need to identify the flawed interface but also need to predict the pattern to identify a secure object like Filename, User Id, or Customer Id, etc.
So let's Begin with how i have found Insecure Direct Object Reference on Nokia:
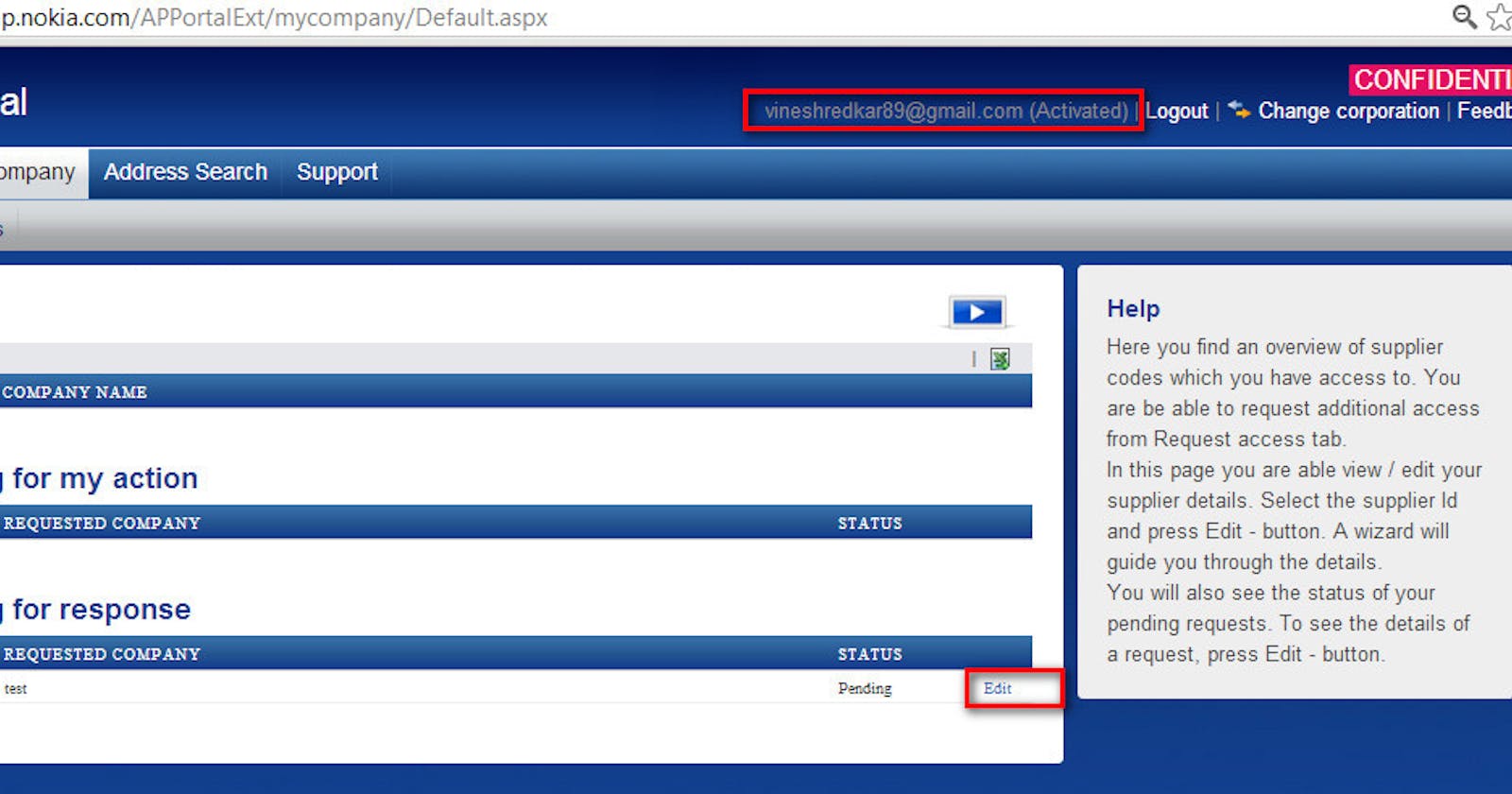
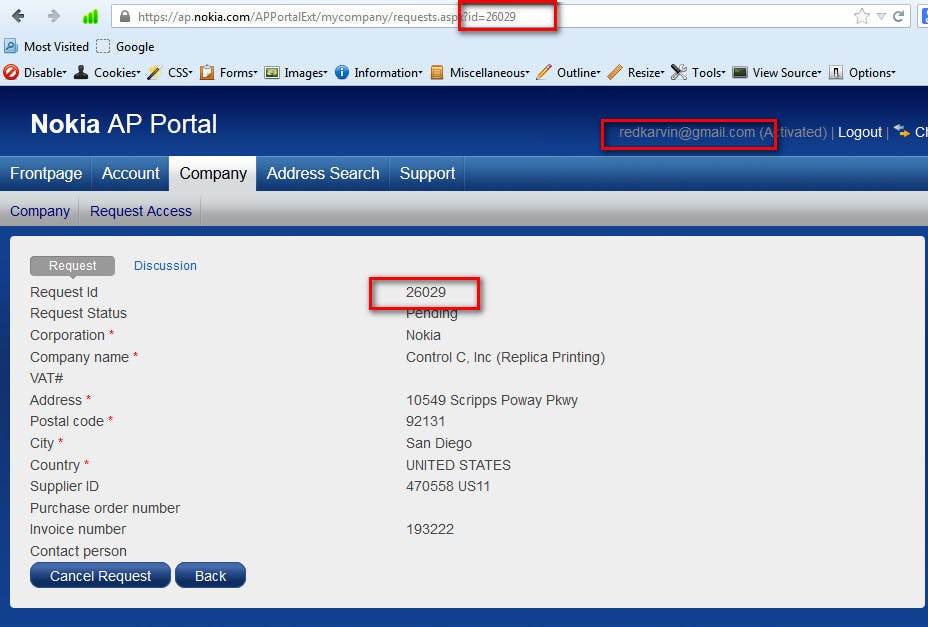
Nokia has a functionality called “Request Details” where the user Request Invoice detail and these details have been saved in the “Requests waiting for response” Section of his profile. This request can be viewed by a User. Below is the URL for the same:
https://ap.nokia.com/APPortalExt/mycompany/requests.aspx?id=28176 Below is the Screenshot For Viewing Data that the User is Allowed to Authorized:
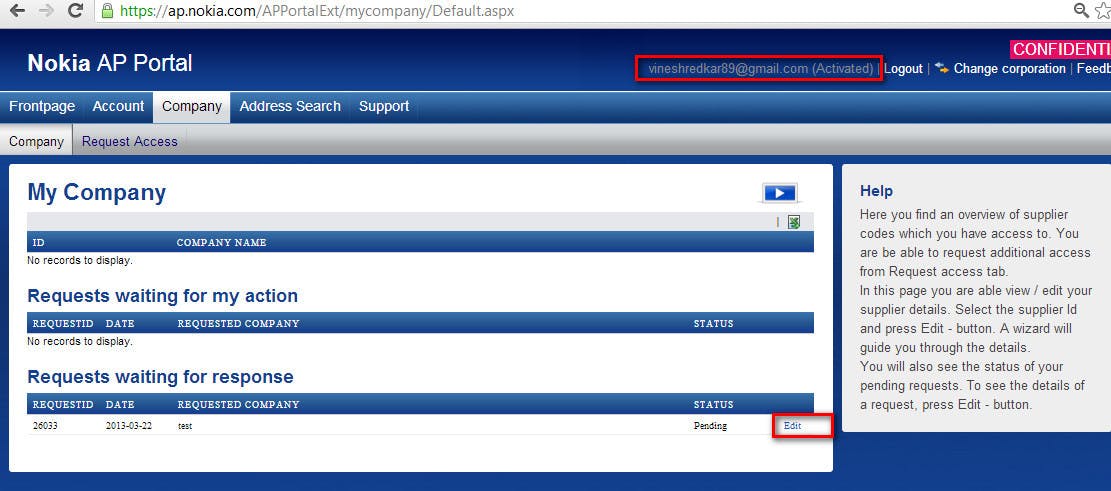
 After analyzing above mentioned URL I have noticed that a parameter id is a number.
After analyzing above mentioned URL I have noticed that a parameter id is a number.
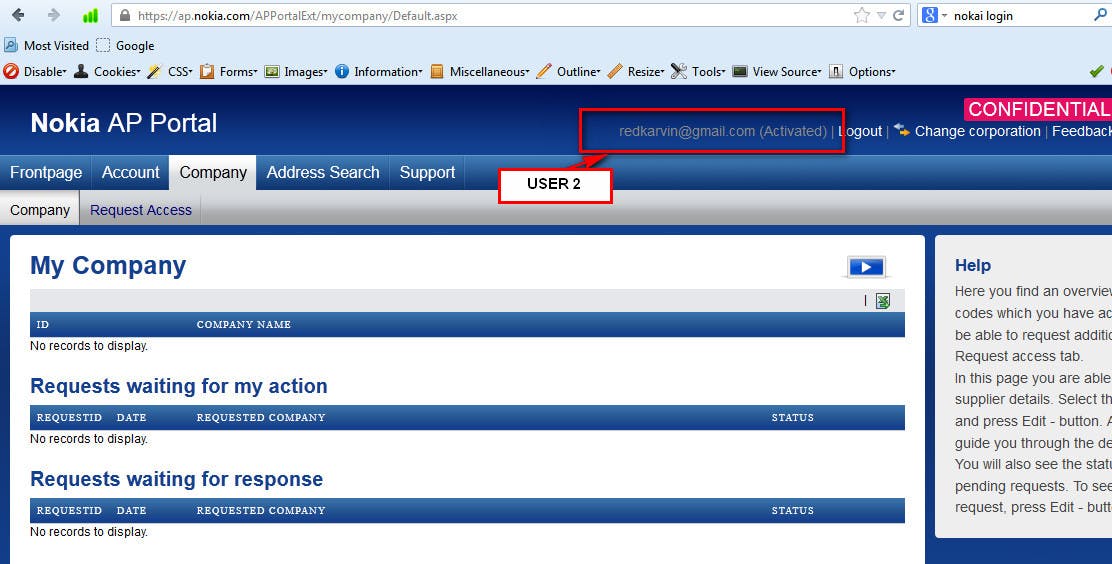
I have easily changed this to a valid request number and I was able to see other Invoice details which were requested by another User.
Below is the Screenshot for Viewing Other User Data which I was not Authorized To
Nokia Response
Nokia Hall Of Fame List
Prevent Insecure Direct Object References : In simple terms, the protection we need is to
- Minimize user ability to predict object IDs/Names
- Don’t expose the actual ID/name of objects
- Verify user authorization each time-sensitive objects/files/contents are accessed
Recent Reply From Nokia (4 Sept 2013)
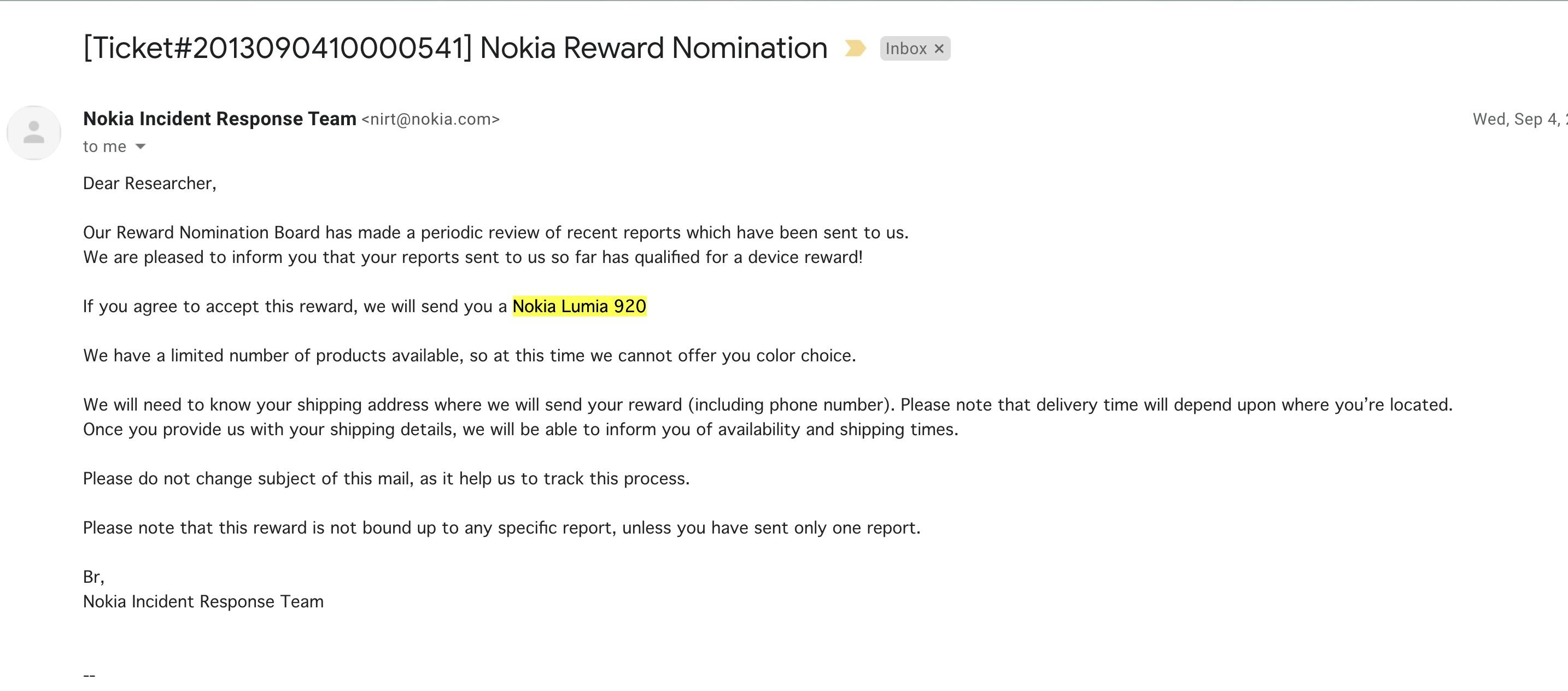
Generous Reward Lumia 920 from Nokia (Fastest Delivery from Nokia Received Within 3day 🙂